More actions
(Created page with "{{Infobox Switch Homebrews |title=Firmware Version Inspector |image=firmwareversioninspectorswitch.png |description=Get FW version from NAND dump. |author=shchmue |lastupdated=2022/11/07 |type=PC Utilities |version=2022 |license=GPL-3.0 |download=https://dlhb.gamebrew.org/switchhomebrews/firmwareversioninspectorswitch.7z |website=https://gbatemp.net/threads/firmware-version-inspector-get-fw-version-from-nand-dump.515308/ |source=https://github.com/shchmue/FVI |donation=...") |
No edit summary |
||
| Line 1: | Line 1: | ||
{{Infobox Switch Homebrews | {{Infobox Switch Homebrews | ||
|title=Firmware Version Inspector | |title=Firmware Version Inspector | ||
|image= | |image=firmwareversioninspectornx.png | ||
|description=Get FW version from NAND dump. | |description=Get FW version from NAND dump. | ||
|author=shchmue | |author=shchmue | ||
|lastupdated= | |lastupdated=2023/04/28 | ||
|type=PC Utilities | |type=PC Utilities | ||
|version=2022 | |version=2022 | ||
|license=GPL-3.0 | |license=GPL-3.0 | ||
|download=https://dlhb.gamebrew.org/switchhomebrews/ | |download=https://dlhb.gamebrew.org/switchhomebrews/firmwareversioninspectornx.7z | ||
|website=https://gbatemp.net/threads/firmware-version-inspector-get-fw-version-from-nand-dump.515308/ | |website=https://gbatemp.net/threads/firmware-version-inspector-get-fw-version-from-nand-dump.515308/ | ||
|source=https://github.com/shchmue/FVI | |source=https://github.com/shchmue/FVI | ||
|donation= | |donation= | ||
}} | }} | ||
Scans a Nintendo Switch NAND dump and identifies its firmware version and whether exFAT is present based on the names of the .nca files in SYSTEM:/Contents/registered. | |||
| | |||
| | '''Author's note:''' Python and command line can be difficult for unfamiliar users, so if possible, it is recommended to use the [[NxNandManager Switch|NxNandManager]] tool, which among other things can list the firmware version of a NAND backup. | ||
| | |||
==User guide== | |||
Requires Python 3 with pycryptodome (pycrypto works too): | |||
pip install pycryptodome | |||
If this is an encrypted backup like Hekate makes (ie. you haven't dumped a decrypted System partition via [[HacDiskMount Switch|HacDiskMount]]), you need to provide your console-specific BIS key 2. Dump this using [[biskeydump Switch|biskeydump]], and save the output to a text file to pass to <code>FVI</code> via the <code>-b</code> option. | |||
Then run from command line: | |||
<pre> | |||
python FVI.py [-b=/path/to/biskeyfile] <dumpfile> | |||
biskeyfile must contain the following lines: | |||
< | BIS Key 2 (crypt): <32-digit hex key> | ||
BIS Key 2 (tweak): <32-digit hex key> | |||
omit -b if System partition already decrypted (eg. dumped with HacDiskMount) | |||
dumpfile must be NAND dump (eg. Hekate rawnand.bin dump) or System partition | |||
</pre> | |||
==Screenshots== | ==Screenshots== | ||
https://dlhb.gamebrew.org/switchhomebrews/ | https://dlhb.gamebrew.org/switchhomebrews/firmwareversioninspectornx2.png | ||
https://dlhb.gamebrew.org/switchhomebrews/ | |||
https://dlhb.gamebrew.org/switchhomebrews/ | https://dlhb.gamebrew.org/switchhomebrews/firmwareversioninspectornx3.png | ||
https://dlhb.gamebrew.org/switchhomebrews/ | |||
https://dlhb.gamebrew.org/switchhomebrews/firmwareversioninspectornx4.png | |||
https:// | https://dlhb.gamebrew.org/switchhomebrews/firmwareversioninspectornx5.png | ||
==Compatibility== | |||
Tested under Windows 10 with Anaconda Python 3.6.5 and Ubuntu 16.04 LTS with Python 3.5.2. | |||
==Credits== | |||
<code>crypto.py</code> module is from [https://github.com/ihaveamac/switchfs/blob/master/switchfs/crypto.py switchfs] under MIT license - it was in turn ported to Python 3 from crypto.py gist by plutooo | |||
Big thanks to the [https://en.wikipedia.org/wiki/Design_of_the_FAT_file_system Wikipedia entry on FAT layout] - being able to read the dump disjointly means FVI only needs to fetch and decrypt a small handful of clusters rather than the entire 2 or 32GB file. | |||
== External links == | == External links == | ||
* | * GitHub - https://github.com/shchmue/FVI | ||
* GBAtemp - https://gbatemp.net/threads/firmware-version-inspector-get-fw-version-from-nand-dump.515308/ | |||
Latest revision as of 04:03, 16 Haziran 2023
| Firmware Version Inspector | |
|---|---|
 | |
| General | |
| Author | shchmue |
| Type | PC Utilities |
| Version | 2022 |
| License | GPL-3.0 |
| Last Updated | 2023/04/28 |
| Links | |
| Download | |
| Website | |
| Source | |
Scans a Nintendo Switch NAND dump and identifies its firmware version and whether exFAT is present based on the names of the .nca files in SYSTEM:/Contents/registered.
Author's note: Python and command line can be difficult for unfamiliar users, so if possible, it is recommended to use the NxNandManager tool, which among other things can list the firmware version of a NAND backup.
User guide
Requires Python 3 with pycryptodome (pycrypto works too):
pip install pycryptodome
If this is an encrypted backup like Hekate makes (ie. you haven't dumped a decrypted System partition via HacDiskMount), you need to provide your console-specific BIS key 2. Dump this using biskeydump, and save the output to a text file to pass to FVI via the -b option.
Then run from command line:
python FVI.py [-b=/path/to/biskeyfile] <dumpfile> biskeyfile must contain the following lines: BIS Key 2 (crypt): <32-digit hex key> BIS Key 2 (tweak): <32-digit hex key> omit -b if System partition already decrypted (eg. dumped with HacDiskMount) dumpfile must be NAND dump (eg. Hekate rawnand.bin dump) or System partition
Screenshots
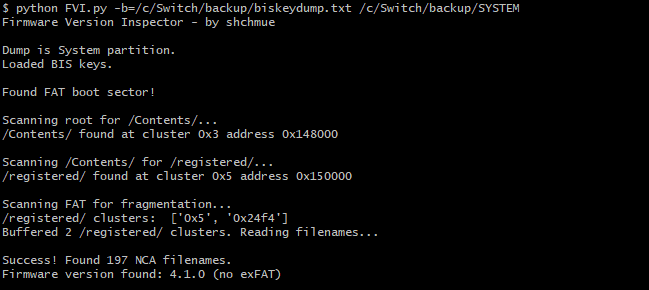
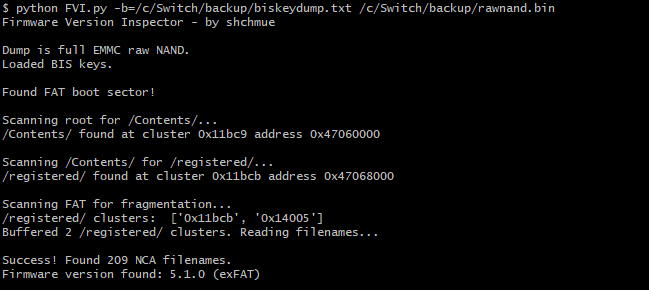
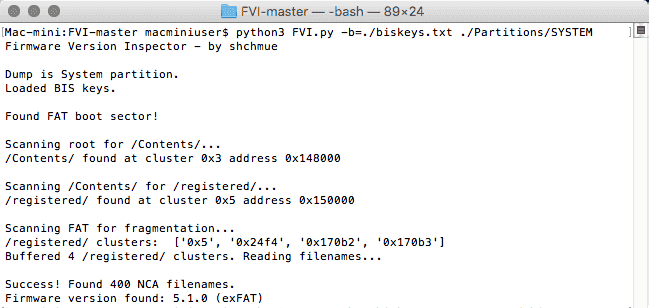
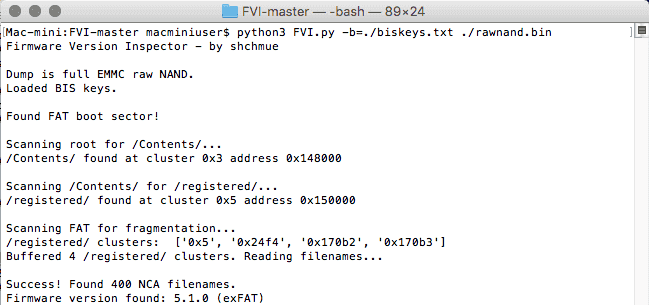
Compatibility
Tested under Windows 10 with Anaconda Python 3.6.5 and Ubuntu 16.04 LTS with Python 3.5.2.
Credits
crypto.py module is from switchfs under MIT license - it was in turn ported to Python 3 from crypto.py gist by plutooo
Big thanks to the Wikipedia entry on FAT layout - being able to read the dump disjointly means FVI only needs to fetch and decrypt a small handful of clusters rather than the entire 2 or 32GB file.
