More actions
No edit summary |
No edit summary |
||
| (17 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
{{Infobox | {{Infobox DS Homebrews | ||
| title | |title=Enigma NDS | ||
| image | |image=enigmands.png | ||
| type | |description=Enigma machine simulator. | ||
| version | |author=mincemeatteam | ||
| | |lastupdated=2011/07/01 | ||
| | |type=Other Apps | ||
| website | |version=1.0 | ||
|license=Mixed | |||
|download=https://dlhb.gamebrew.org/dshomebrew2/enigmands_1.0.zip | |||
}} | |website=http://mincemeatteam.eshost.es/enigma.php | ||
}} | |||
EnigmaNDS is a simulator of the Enigma machine. | |||
It was a contest entry to the Scenery Beta 2011 (NDS Applications, 3rd place). | |||
==User guide== | |||
The Enigma machine was used by the Germans to encrypt their communications during the 2nd World War. It was a machine based on rotary substitution encryption. | |||
It | EnigmaNDS simulates the original version of the Enigma, which operated with 3 rotors selected from 5 possibilities. It allows you to configure the rotor position and number, and also simulates the function of the steckers (a front panel that allowed for a preliminary permutation before encryption). | ||
Theoretically the application can encrypt text with a key (rotors, initial position of the rotors and configuration of the steckers). If later, the text shown above, the ciphertext is re-encrypted with the same key, you get the original text. | |||
That is, if HELLO is encrypted, the machine encrypts it as OIIQ. If you put the rotors back in the position for the encrypted code OIIQ, the screen would appear the decrypted text: HELLO. | |||
==Controls== | |||
Operate with Stylus. | |||
==Screenshots== | |||
https://dlhb.gamebrew.org/dshomebrew/enigmands2.png | |||
https://dlhb.gamebrew.org/dshomebrew/enigmands3.png | |||
== | ==External links== | ||
* Author's website - http://mincemeatteam.eshost.es/enigma.php | |||
* SceneBeta - https://nds.scenebeta.com/noticia/enigmands | |||
[[Category: | [[Category:Scenery Beta 2011]] | ||
Latest revision as of 12:51, 20 August 2024
| Enigma NDS | |
|---|---|
 | |
| General | |
| Author | mincemeatteam |
| Type | Other Apps |
| Version | 1.0 |
| License | Mixed |
| Last Updated | 2011/07/01 |
| Links | |
| Download | |
| Website | |
EnigmaNDS is a simulator of the Enigma machine.
It was a contest entry to the Scenery Beta 2011 (NDS Applications, 3rd place).
User guide
The Enigma machine was used by the Germans to encrypt their communications during the 2nd World War. It was a machine based on rotary substitution encryption.
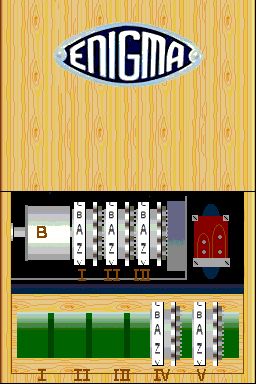
EnigmaNDS simulates the original version of the Enigma, which operated with 3 rotors selected from 5 possibilities. It allows you to configure the rotor position and number, and also simulates the function of the steckers (a front panel that allowed for a preliminary permutation before encryption).
Theoretically the application can encrypt text with a key (rotors, initial position of the rotors and configuration of the steckers). If later, the text shown above, the ciphertext is re-encrypted with the same key, you get the original text.
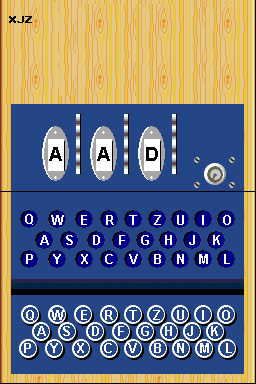
That is, if HELLO is encrypted, the machine encrypts it as OIIQ. If you put the rotors back in the position for the encrypted code OIIQ, the screen would appear the decrypted text: HELLO.
Controls
Operate with Stylus.
Screenshots
External links
- Author's website - http://mincemeatteam.eshost.es/enigma.php
- SceneBeta - https://nds.scenebeta.com/noticia/enigmands
