More actions
(Created page with "{{Infobox Switch Homebrews |title=Hactool |image=hactoolswitch.png |description=hactool is a tool to view information about, decrypt, and extract common file formats for the Nintendo Switch, especially Nintendo Content Archives. |author=SciresM |lastupdated=2020/06/02 |type=PC Utilities |version=1.4.0 |license=ISC |download=https://dlhb.gamebrew.org/switchhomebrews/hactoolswitch.7z |website=https://github.com/SciresM/hactool |source=https://github.com/SciresM/hactool |do...") |
No edit summary |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
{{Infobox Switch Homebrews | {{Infobox Switch Homebrews | ||
|title=Hactool | |title=Hactool | ||
|image= | |image=hactoolnx.png | ||
|description= | |description=A tool to view information about, decrypt, and extract common file formats for the Nintendo Switch, especially Nintendo Content Archives. | ||
|author=SciresM | |author=SciresM | ||
|lastupdated=2020/06/02 | |lastupdated=2020/06/02 | ||
| Line 8: | Line 8: | ||
|version=1.4.0 | |version=1.4.0 | ||
|license=ISC | |license=ISC | ||
|download=https://dlhb.gamebrew.org/switchhomebrews/ | |download=https://dlhb.gamebrew.org/switchhomebrews/hactoolnx.7z | ||
|website=https:// | |website=https://gbatemp.net/threads/hactool-release-by-sciresm.496146/ | ||
|source=https://github.com/SciresM/hactool | |source=https://github.com/SciresM/hactool | ||
|donation= | |donation= | ||
}} | }} | ||
hactool is a tool to view information about, decrypt, and extract common file formats for the Nintendo Switch, especially Nintendo Content Archives. | |||
It is heavily inspired by [https://github.com/profi200/Project_CTR/tree/master/ctrtool ctrtool]. | |||
==Features== | ==Features== | ||
*Support for reading plaintext Package2 files | *View information about, decrypt, and extract common file formats for the Nintendo Switch. | ||
*NPDM | *Support for reading plaintext Package2 files. | ||
*KIP1 | *NPDM > JSON conversion. | ||
*KIP1 > JSON conversion. | |||
*Keygen can now be performed without passing a BOOT0 file. | *Keygen can now be performed without passing a BOOT0 file. | ||
*Support for newer XCIs with a logo partition | *Support for newer XCIs with a logo partition. | ||
*Support for pre-1.0.0 NCA0 files | *Support for pre-1.0.0 NCA0 files. | ||
*Support for uncompressing NSO0 and KIP1 files | *Support for uncompressing NSO0 and KIP1 files via --uncompressed= | ||
*Titlekeys can | *Titlekeys can be loaded from an external "title.keys" file, located in the same directory as prod.keys or dev.keys. -Titlekeys should be stored in the format hexadecimal_rights_id = hexadecimal_title_key. | ||
*Various [WARN]s | *Various [WARN]s when odd behavior is detected. | ||
* | *Support for NAX0 (Nintendo Aes Xts File(system), SD Card content). | ||
* | *Support for key derivation using EKS (keyblobs) and sbk/tsec key. | ||
*Support | *Support for pre-1.0.0 "NCA2" content. | ||
== | ==User guide== | ||
===Supported Switch file formats=== | |||
{| style="margin-left:0em;" | |||
| | |||
*NCA | *NCA | ||
*XCI | *XCI | ||
| Line 41: | Line 41: | ||
*PFS0 | *PFS0 | ||
*RomFS | *RomFS | ||
*Package1 (PK11) | *Package1 (PK11) | ||
*Package2 (PK21) | *Package2 (PK21) | ||
|width="10px"| <!--spacer-column--> | |||
| | |||
*NPDM | |||
*INI1 | *INI1 | ||
*KIP1 | *KIP1 | ||
| Line 49: | Line 51: | ||
*NSO0 | *NSO0 | ||
*Save files | *Save files | ||
|} | |||
==Usage== | ===Usage=== | ||
<pre> | <pre> | ||
Usage: hactool [options...] <file> | Usage: hactool [options...] <file> | ||
| Line 135: | Line 138: | ||
</pre> | </pre> | ||
== | ==External Keys== | ||
External keys can be provided by the -k/--keyset argument to the a keyset filename. Keyset files are text files containing one key per line, in the form "key_name = HEXADECIMALKEY". Case shouldn't matter, nor should whitespace. | |||
In addition, if -k/--keyset is not set, hactool will check for the presence of a keyset file in $HOME/.switch/prod.keys (or $HOME/.switch/dev.keys if -d/--dev is set). If present, this file will automatically be loaded. | |||
==Screenshots== | |||
{| style="width: 90%; margin-left:0em;" | |||
| | |||
https://dlhb.gamebrew.org/switchhomebrews/hactoolnx2.png | |||
|} | |||
==Media== | ==Media== | ||
'''Decrypting Switch Firmwares with hactool: a tutorial | '''Decrypting Switch Firmwares with hactool: a tutorial ([https://www.youtube.com/watch?v=YHSDXVZxedU (C)ode e(X)ecute])'''<br> | ||
<youtube>YHSDXVZxedU</youtube> | <youtube>YHSDXVZxedU</youtube> | ||
==Changelog== | ==Changelog== | ||
''' | '''v1.4.0 2020/06/02''' | ||
*Support was fixed for parsing save files (thanks @shchmue) | *Support was fixed for parsing save files (thanks @shchmue). | ||
*Support was fixed for extracting package1 binaries newer than 4.0.0. | *Support was fixed for extracting package1 binaries newer than 4.0.0. | ||
*Support was added for performing mariko-specific key derivation. | *Support was added for performing mariko-specific key derivation. | ||
*Support was added for decrypting and extracting mariko package1 binaries. | *Support was added for decrypting and extracting mariko package1 binaries. | ||
''' | '''v1.3.3 2020/04/06''' | ||
*Support was added for parsing Chinese game cards, which use a new hashing algorithm to validate HFS0 partitions. | *Support was added for parsing Chinese game cards, which use a new hashing algorithm to validate HFS0 partitions. | ||
''' | '''v1.3.2 3030/03/19''' | ||
*Support was added for validating new NCA header fixed-keys (9.x+) | *Support was added for validating new NCA header fixed-keys (9.x+). | ||
*Romfs is now parsed via an iterative loop instead of recursion to prevent possible stack exhaustion. | *Romfs is now parsed via an iterative loop instead of recursion to prevent possible stack exhaustion. | ||
''' | '''v1.3.1 2020/02/22''' | ||
*Output was fixed for displaying certain SDK versions. | *Output was fixed for displaying certain SDK versions. | ||
*Support was added for validating new ACID keys (9.x+) | *Support was added for validating new ACID keys (9.x+). | ||
''' | '''v1.3.0 2020/01/16''' | ||
*Support was fixed for new (8.0.0+) key generation. | *Support was fixed for new (8.0.0+) key generation. | ||
*Support was added for extracting 8.0.0+ Package2 binaries. | *Support was added for extracting 8.0.0+ Package2 binaries. | ||
*SVC and key generation names were updated to latest definitions. | *SVC and key generation names were updated to latest definitions. | ||
*Support was added for parsing and extracting save files (thanks @shchmue | *Support was added for parsing and extracting save files (thanks @shchmue). | ||
*Support was added for decrypting and parsing the encrypted XCI header area (thanks @jakcron | *Support was added for decrypting and parsing the encrypted XCI header area (thanks @jakcron). | ||
*NPDM output was corrected when parsing the version field. | *NPDM output was corrected when parsing the version field. | ||
*Support was added for suppressing output of sensitive/decrypted keys. | *Support was added for suppressing output of sensitive/decrypted keys. | ||
| Line 176: | Line 181: | ||
*Support was added for skipping output of invalid key warnings. | *Support was added for skipping output of invalid key warnings. | ||
*A bug was fixed that caused PFS0 file entry calculations to fail. | *A bug was fixed that caused PFS0 file entry calculations to fail. | ||
''' | '''v1.2.2 2018/11/24''' | ||
*Support was added for 6.2.0+ new key derivation using tsec_root_key and master_kek_source_##. | *Support was added for 6.2.0+ new key derivation using tsec_root_key and master_kek_source_##. | ||
*6.2.0 keydata will no longer be called "Unknown". | *6.2.0 keydata will no longer be called "Unknown". | ||
*A bug was fixed involving argument violation to mbed_tls aes routines. | *A bug was fixed involving argument violation to mbed_tls aes routines. | ||
''' | '''v1.2.1 2018/11/04''' | ||
*Update extraction support should no longer cause errors. | *Update extraction support should no longer cause errors. | ||
*NPDM JSON output has been switched over to the new format. | *NPDM JSON output has been switched over to the new format. | ||
*6.x keydata will no longer be called "Unknown". | *6.x keydata will no longer be called "Unknown". | ||
''' | '''v1.2.0 2018/07/24''' | ||
*NAX0 decryption failed when reading at unaligned offsets. | *New Features: | ||
*NCAs making use of AES-XTS crypto are no longer completely broken | **Support for reading plaintext Package2 files was added. | ||
*Support for pre-1.0.0 NCA2 files was fixed, and now works properly | **NPDM -> JSON conversion was added. | ||
*Getopt is no longer broken on arm-linux (thanks @jakibaki | **KIP1 -> JSON conversion was added. | ||
*Too many small ones to count : | **Keygen can now be performed without passing a BOOT0 file. | ||
*"encrypted_header_key" was changed in keyset loading to "header_key_source", in order to be consistent with other key names. | **Support for newer XCIs with a logo partition was added. | ||
''' | **Support for pre-1.0.0 NCA0 files was added. | ||
*BKTR did not support the non-single bucket case, affecting games with huge patches (Splatoon 2, maybe others) | **Support for uncompressing NSO0 and KIP1 files was added via --uncompressed= | ||
*Too many small ones to count | **Titlekeys can now be loaded from an external "title.keys" file, located in the same directory as prod.keys or dev.keys. Titlekeys should be stored in the format hexadecimal_rights_id = hexadecimal_title_key. | ||
''' | **Various [WARN]s were added when odd behavior is detected. | ||
*Memory corruption when parsing some NPDMs | *Bugs fixed: | ||
*Invalid AES mode used for titlekey decryption | **NAX0 decryption failed when reading at unaligned offsets. | ||
*BKTR section validity unchecked before accessing decrypted data | **NCAs making use of AES-XTS crypto are no longer completely broken. | ||
*Edge case in BKTR subsection layout would cause infinite recursion | **Support for pre-1.0.0 NCA2 files was fixed, and now works properly. | ||
''' | **Getopt is no longer broken on arm-linux (thanks @jakibaki). | ||
**Too many small ones to count. | |||
*Breaking changes: | |||
**"encrypted_header_key" was changed in keyset loading to "header_key_source", in order to be consistent with other key names. | |||
'''v1.1.0 2018/04/28''' | |||
*New Features: | |||
**Added support for NAX0 (Nintendo Aes Xts File(system), SD Card content). | |||
**Added support for key derivation using EKS (keyblobs) and sbk/tsec key. | |||
**Support was added for pre-1.0.0 "NCA2" content. | |||
*Bugs fixed: | |||
**BKTR did not support the non-single bucket case, affecting games with huge patches (Splatoon 2, maybe others). | |||
**Too many small ones to count. | |||
'''v1.0.1 2018/02/08''' | |||
*Bugs fixed: | |||
**Memory corruption when parsing some NPDMs. | |||
**Invalid AES mode used for titlekey decryption. | |||
**BKTR section validity unchecked before accessing decrypted data. | |||
**Edge case in BKTR subsection layout would cause infinite recursion. | |||
'''v1.0 2018/02/07''' | |||
* First Release. | * First Release. | ||
== External links == | == External links == | ||
* | * GitHub - https://github.com/SciresM/hactool | ||
* GBAtemp - https://gbatemp.net/threads/hactool-release-by-sciresm.496146/ | |||
Latest revision as of 13:33, 4 August 2023
| Hactool | |
|---|---|
 | |
| General | |
| Author | SciresM |
| Type | PC Utilities |
| Version | 1.4.0 |
| License | ISC |
| Last Updated | 2020/06/02 |
| Links | |
| Download | |
| Website | |
| Source | |
hactool is a tool to view information about, decrypt, and extract common file formats for the Nintendo Switch, especially Nintendo Content Archives.
It is heavily inspired by ctrtool.
Features
- View information about, decrypt, and extract common file formats for the Nintendo Switch.
- Support for reading plaintext Package2 files.
- NPDM > JSON conversion.
- KIP1 > JSON conversion.
- Keygen can now be performed without passing a BOOT0 file.
- Support for newer XCIs with a logo partition.
- Support for pre-1.0.0 NCA0 files.
- Support for uncompressing NSO0 and KIP1 files via --uncompressed=
- Titlekeys can be loaded from an external "title.keys" file, located in the same directory as prod.keys or dev.keys. -Titlekeys should be stored in the format hexadecimal_rights_id = hexadecimal_title_key.
- Various [WARN]s when odd behavior is detected.
- Support for NAX0 (Nintendo Aes Xts File(system), SD Card content).
- Support for key derivation using EKS (keyblobs) and sbk/tsec key.
- Support for pre-1.0.0 "NCA2" content.
User guide
Supported Switch file formats
|
|
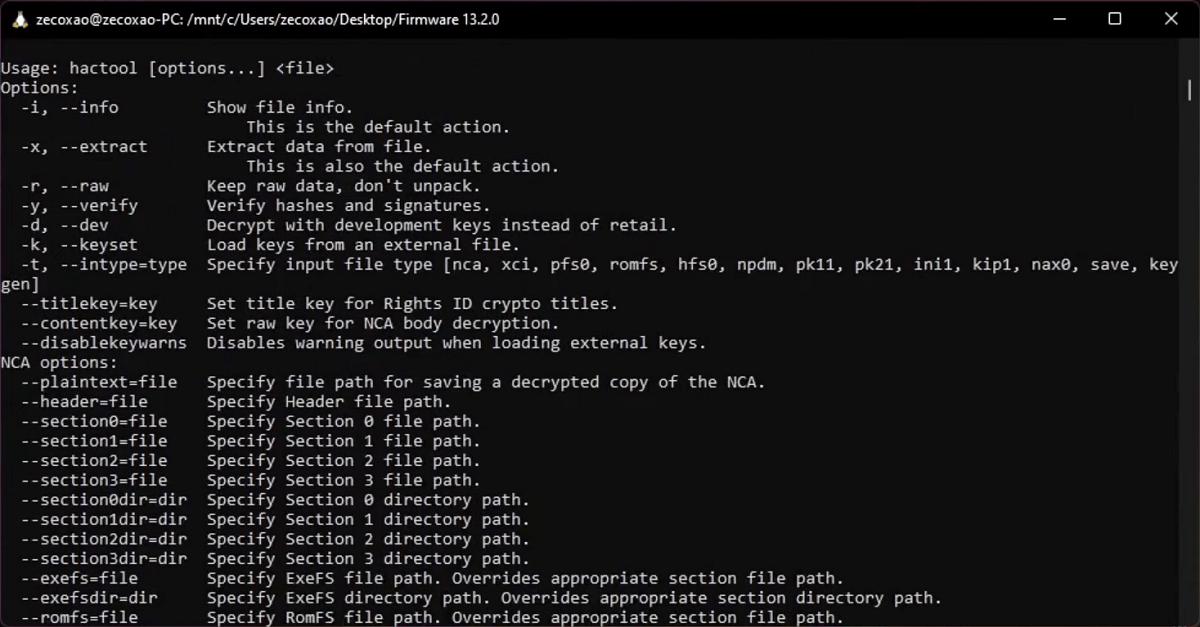
Usage
Usage: hactool [options...] <file>
Options:
-i, --info Show file info.
This is the default action.
-x, --extract Extract data from file.
This is also the default action.
-r, --raw Keep raw data, don't unpack.
-y, --verify Verify hashes and signatures.
-d, --dev Decrypt with development keys instead of retail.
-k, --keyset Load keys from an external file.
-t, --intype=type Specify input file type [nca, xci, pfs0, romfs, hfs0, npdm, pk11, pk21, ini1, kip1, nax0, save, keygen]
--titlekey=key Set title key for Rights ID crypto titles.
--contentkey=key Set raw key for NCA body decryption.
--disablekeywarns Disables warning output when loading external keys.
NCA options:
--plaintext=file Specify file path for saving a decrypted copy of the NCA.
--header=file Specify Header file path.
--section0=file Specify Section 0 file path.
--section1=file Specify Section 1 file path.
--section2=file Specify Section 2 file path.
--section3=file Specify Section 3 file path.
--section0dir=dir Specify Section 0 directory path.
--section1dir=dir Specify Section 1 directory path.
--section2dir=dir Specify Section 2 directory path.
--section3dir=dir Specify Section 3 directory path.
--exefs=file Specify ExeFS file path. Overrides appropriate section file path.
--exefsdir=dir Specify ExeFS directory path. Overrides appropriate section directory path.
--romfs=file Specify RomFS file path. Overrides appropriate section file path.
--romfsdir=dir Specify RomFS directory path. Overrides appropriate section directory path.
--listromfs List files in RomFS.
--baseromfs Set Base RomFS to use with update partitions.
--basenca Set Base NCA to use with update partitions.
--basefake Use a fake Base RomFS with update partitions (all reads will return 0xCC).
--onlyupdated Ignore non-updated files in update partitions.
NPDM options:
--json=file Specify file path for saving JSON representation of program permissions to.
KIP1 options:
--json=file Specify file path for saving JSON representation of program permissions to.
--uncompressed=f Specify file path for saving uncompressed KIP1.
NSO0 options:
--uncompressed=f Specify file path for saving uncompressed NSO0.
PFS0 options:
--pfs0dir=dir Specify PFS0 directory path.
--outdir=dir Specify PFS0 directory path. Overrides previous path, if present.
--exefsdir=dir Specify PFS0 directory path. Overrides previous paths, if present for ExeFS PFS0.
RomFS options:
--romfsdir=dir Specify RomFS directory path.
--outdir=dir Specify RomFS directory path. Overrides previous path, if present.
--listromfs List files in RomFS.
HFS0 options:
--hfs0dir=dir Specify HFS0 directory path.
--outdir=dir Specify HFS0 directory path. Overrides previous path, if present.
--exefsdir=dir Specify HFS0 directory path. Overrides previous paths, if present.
XCI options:
--rootdir=dir Specify XCI root HFS0 directory path.
--updatedir=dir Specify XCI update HFS0 directory path.
--normaldir=dir Specify XCI normal HFS0 directory path.
--securedir=dir Specify XCI secure HFS0 directory path.
--logodir=dir Specify XCI logo HFS0 directory path.
--outdir=dir Specify XCI directory path. Overrides previous paths, if present.
Package1 options:
--package1dir=dir Specify Package1 directory path.
--outdir=dir Specify Package1 directory path. Overrides previous path, if present.
Package2 options:
--package2dir=dir Specify Package2 directory path.
--outdir=dir Specify Package2 directory path. Overrides previous path, if present.
--extractini1 Enable INI1 extraction to default directory (redundant with --ini1dir set).
--ini1dir=dir Specify INI1 directory path. Overrides default path, if present.
INI1 options:
--ini1dir=dir Specify INI1 directory path.
--outdir=dir Specify INI1 directory path. Overrides previous path, if present.
--saveini1json Enable generation of JSON descriptors for all INI1 members.
NAX0 options:
--sdseed=seed Set console unique seed for SD card NAX0 encryption.
--sdpath=path Set relative path for NAX0 key derivation (ex: /registered/000000FF/cafebabecafebabecafebabecafebabe.nca).
Save data options:
--outdir=dir Specify save directory path.
--listfiles List files in save file.
Key Derivation options:
--sbk=key Set console unique Secure Boot Key for key derivation.
--tseckey=key Set console unique TSEC Key for key derivation.```
External Keys
External keys can be provided by the -k/--keyset argument to the a keyset filename. Keyset files are text files containing one key per line, in the form "key_name = HEXADECIMALKEY". Case shouldn't matter, nor should whitespace.
In addition, if -k/--keyset is not set, hactool will check for the presence of a keyset file in $HOME/.switch/prod.keys (or $HOME/.switch/dev.keys if -d/--dev is set). If present, this file will automatically be loaded.
Screenshots
|
|
Media
Decrypting Switch Firmwares with hactool: a tutorial ((C)ode e(X)ecute)
Changelog
v1.4.0 2020/06/02
- Support was fixed for parsing save files (thanks @shchmue).
- Support was fixed for extracting package1 binaries newer than 4.0.0.
- Support was added for performing mariko-specific key derivation.
- Support was added for decrypting and extracting mariko package1 binaries.
v1.3.3 2020/04/06
- Support was added for parsing Chinese game cards, which use a new hashing algorithm to validate HFS0 partitions.
v1.3.2 3030/03/19
- Support was added for validating new NCA header fixed-keys (9.x+).
- Romfs is now parsed via an iterative loop instead of recursion to prevent possible stack exhaustion.
v1.3.1 2020/02/22
- Output was fixed for displaying certain SDK versions.
- Support was added for validating new ACID keys (9.x+).
v1.3.0 2020/01/16
- Support was fixed for new (8.0.0+) key generation.
- Support was added for extracting 8.0.0+ Package2 binaries.
- SVC and key generation names were updated to latest definitions.
- Support was added for parsing and extracting save files (thanks @shchmue).
- Support was added for decrypting and parsing the encrypted XCI header area (thanks @jakcron).
- NPDM output was corrected when parsing the version field.
- Support was added for suppressing output of sensitive/decrypted keys.
- Support was added for only extracting NCAs if the content type is one specified.
- Support was added for automatically appending the NCA section type to extracted section content paths if an option is specified.
- Key derivation was fixed when deriving master keks from keyblobs.
- title.keys content restrictions were made looser (non-key lines are now allowed).
- Support was added for skipping output of invalid key warnings.
- A bug was fixed that caused PFS0 file entry calculations to fail.
v1.2.2 2018/11/24
- Support was added for 6.2.0+ new key derivation using tsec_root_key and master_kek_source_##.
- 6.2.0 keydata will no longer be called "Unknown".
- A bug was fixed involving argument violation to mbed_tls aes routines.
v1.2.1 2018/11/04
- Update extraction support should no longer cause errors.
- NPDM JSON output has been switched over to the new format.
- 6.x keydata will no longer be called "Unknown".
v1.2.0 2018/07/24
- New Features:
- Support for reading plaintext Package2 files was added.
- NPDM -> JSON conversion was added.
- KIP1 -> JSON conversion was added.
- Keygen can now be performed without passing a BOOT0 file.
- Support for newer XCIs with a logo partition was added.
- Support for pre-1.0.0 NCA0 files was added.
- Support for uncompressing NSO0 and KIP1 files was added via --uncompressed=
- Titlekeys can now be loaded from an external "title.keys" file, located in the same directory as prod.keys or dev.keys. Titlekeys should be stored in the format hexadecimal_rights_id = hexadecimal_title_key.
- Various [WARN]s were added when odd behavior is detected.
- Bugs fixed:
- NAX0 decryption failed when reading at unaligned offsets.
- NCAs making use of AES-XTS crypto are no longer completely broken.
- Support for pre-1.0.0 NCA2 files was fixed, and now works properly.
- Getopt is no longer broken on arm-linux (thanks @jakibaki).
- Too many small ones to count.
- Breaking changes:
- "encrypted_header_key" was changed in keyset loading to "header_key_source", in order to be consistent with other key names.
v1.1.0 2018/04/28
- New Features:
- Added support for NAX0 (Nintendo Aes Xts File(system), SD Card content).
- Added support for key derivation using EKS (keyblobs) and sbk/tsec key.
- Support was added for pre-1.0.0 "NCA2" content.
- Bugs fixed:
- BKTR did not support the non-single bucket case, affecting games with huge patches (Splatoon 2, maybe others).
- Too many small ones to count.
v1.0.1 2018/02/08
- Bugs fixed:
- Memory corruption when parsing some NPDMs.
- Invalid AES mode used for titlekey decryption.
- BKTR section validity unchecked before accessing decrypted data.
- Edge case in BKTR subsection layout would cause infinite recursion.
v1.0 2018/02/07
- First Release.