More actions
No edit summary |
No edit summary |
||
| (7 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
{{Infobox Wii Homebrews | {{Infobox Wii Homebrews | ||
|title=Wilbrand | |title=Wilbrand | ||
|image= | |image=wilbrand3.png | ||
|description= | |description=A program used to build the mailbox bomb exploit for the Wii system menu. | ||
|author=giantpune | |author=giantpune | ||
|lastupdated=2012/04/17 | |lastupdated=2012/04/17 | ||
|type=Exploits | |type=Exploits | ||
|version= | |version=3 | ||
|license=GPL-2.0 | |license=GPL-2.0 | ||
|download=https://dlhb.gamebrew.org/wiihomebrews/ | |download=https://dlhb.gamebrew.org/wiihomebrews/wilbrand.7z | ||
|website=https://wiidatabase.de/downloads/exploits/wilbrand/ | |website=https://wiidatabase.de/downloads/exploits/wilbrand/ | ||
|source=https://github.com/giantpune/mailboxbomb | |source=https://github.com/giantpune/mailboxbomb | ||
}} | }} | ||
Wilbrand is a exploit for the Wii | Wilbrand is a exploit for the Wii Message Board. Similar to [[LetterBomb Wii|LetterBomb]], it works on system menus from 3.0 to 4.3. | ||
== | The tool is operated through the command line and includes an executable for Windows and a binary for Unix-like systems. | ||
This is a cli program | |||
== User guide == | |||
This is a cli program. Here is the usage: | |||
<pre>Wilbrand <MAC address> <date> <sysmenu version> <SD Root></pre> | <pre>Wilbrand <MAC address> <date> <sysmenu version> <SD Root></pre> | ||
| Line 29: | Line 25: | ||
! Definition | ! Definition | ||
|- | |- | ||
! MAC Address | |||
| The wireless MAC address of the wii. you can get this from the internet settings, or if those are inaccessible for whatever reason, many routers will display it. It may contain dashes, colons, or spaces, but should be 12 hex characters when these extra characters are removed. | | The wireless MAC address of the wii. you can get this from the internet settings, or if those are inaccessible for whatever reason, many routers will display it. It may contain dashes, colons, or spaces, but should be 12 hex characters when these extra characters are removed. | ||
|- | |- | ||
! Date | |||
| this is the date you want the message to show up under in the message board. It should be within the range of 2000 - 2035. Accepted formats are mm/dd/yyyy or in a 32bit hex representation of the number of seconds since 00:00 Jan, 01 2000. NOTE The System menu is triggered to load messages from the SD card when you scroll across days. So if you build the message for the current day, you will have to scroll to a different day and then back again to trigger the loading of it. | | this is the date you want the message to show up under in the message board. It should be within the range of 2000 - 2035. Accepted formats are mm/dd/yyyy or in a 32bit hex representation of the number of seconds since 00:00 Jan, 01 2000. NOTE The System menu is triggered to load messages from the SD card when you scroll across days. So if you build the message for the current day, you will have to scroll to a different day and then back again to trigger the loading of it. | ||
|- | |- | ||
! SysmenuVersion | |||
| This is the version of the System menu to build the exploit for. It can be read in the first page under Wii settings. Accepted formats are 3.2u, 32u, 3.2U, and 32U. Accepted versions are any official, publicly released version from 3.0 - 4.3. | | This is the version of the System menu to build the exploit for. It can be read in the first page under Wii settings. Accepted formats are 3.2u, 32u, 3.2U, and 32U. Accepted versions are any official, publicly released version from 3.0 - 4.3. | ||
|- | |- | ||
! SD Root | |||
| This is the base folder where you would like the message created. The design of the cdb archive uses about 13 subfolders to store files. This program will use the given folder and create the necessary folder structure and then place the exploit message in its place. | | This is the base folder where you would like the message created. The design of the cdb archive uses about 13 subfolders to store files. This program will use the given folder and create the necessary folder structure and then place the exploit message in its place. | ||
|} | |} | ||
Examples: | '''Examples:''' | ||
./Wilbrand 001122334455 10/25/2011 3.2u /media/sdcard | ./Wilbrand 001122334455 10/25/2011 3.2u /media/sdcard | ||
| Line 50: | Line 46: | ||
./Wilbrand '00 11 22 33 44 55' 163a09c4 4.3K F: | ./Wilbrand '00 11 22 33 44 55' 163a09c4 4.3K F: | ||
You need to use an SD card that is supported by your system menu version. To test this, go to the data management or SD card menu and try to use the SD card | You need to use an SD card that is supported by your system menu version. To test this, go to the data management or SD card menu and try to use the SD card. | ||
It will tell you if it can't be used. Once you have run this program, and have the exploit message on your SD card, you need some homebrew to load. [http://bootmii.org/download/ This one] works pretty well. Save the homebrew as SD:/boot.elf. | |||
Then stick the SD card in your Wii, start it up, go to the message board, and then scroll to the day that the exploit was built for. It should be easily identifiable as it will be the best looking envelope there. Click it and watch the magic happen. | |||
==Screenshots== | |||
https://dlhb.gamebrew.org/wiihomebrews/wilbrand3.png | |||
=== FAQ === | |||
'''Q. I can't run the program./Wilbrand just gives me errors and doesn't build the exploit.''' | |||
Read and re-read the usage instructions. Google how to use a cli program. | |||
'''Q. I don't see the incredibly cool image.''' | |||
Double check that you are looking at the date you gave to wilbrand when building the exploit. | |||
Make sure the system menu can access your SD card. | |||
Make sure you gave the correct WIRELESS MAC address to the program. | |||
'''Q. When I click the message, it freezes.''' | |||
You gave the wrong system menu version when building the exploit message. | |||
'''Q. I click the message and I get a black screen with white text flying by over and over.''' | |||
Make sure you have SD:/boot.elf. Try with a different SD card. Apparently this SD code doesn't like some cards. | |||
== Changelog == | == Changelog == | ||
| Line 88: | Line 80: | ||
*Initial public release. | *Initial public release. | ||
== | ==Credits== | ||
Authors: | |||
*Hackmii team - Savezelda's loader was used as a starting point for the payload. | *Hackmii team - Savezelda's loader was used as a starting point for the payload. | ||
*Paul E. Jones - sha1 code | *Paul E. Jones - sha1 code. | ||
*Mike Scott - AES code | *Mike Scott - AES code. | ||
* | *Others - there is some misc code involved (such as wbe32()) that was takes from various open-source projects which was very nice to have, but I'm sure I couldn't name all occurances and credit all authors appropriately. | ||
*giantpune - finding the initial bug [WOOHOO!], dumping and debugging 32 version of the system menu to find the offsets, pretty much everything else involved | *giantpune - finding the initial bug [WOOHOO!], dumping and debugging 32 version of the system menu to find the offsets, pretty much everything else involved. | ||
== | ==External links== | ||
* GitHub - https://github.com/giantpune/mailboxbomb | |||
* Wiidatabase - https://wiidatabase.de/downloads/exploits/wilbrand/ | |||
Latest revision as of 15:41, 3 August 2023
| Wilbrand | |
|---|---|
 | |
| General | |
| Author | giantpune |
| Type | Exploits |
| Version | 3 |
| License | GPL-2.0 |
| Last Updated | 2012/04/17 |
| Links | |
| Download | |
| Website | |
| Source | |
Wilbrand is a exploit for the Wii Message Board. Similar to LetterBomb, it works on system menus from 3.0 to 4.3.
The tool is operated through the command line and includes an executable for Windows and a binary for Unix-like systems.
User guide
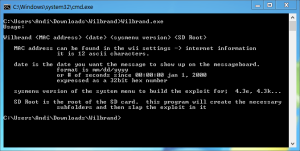
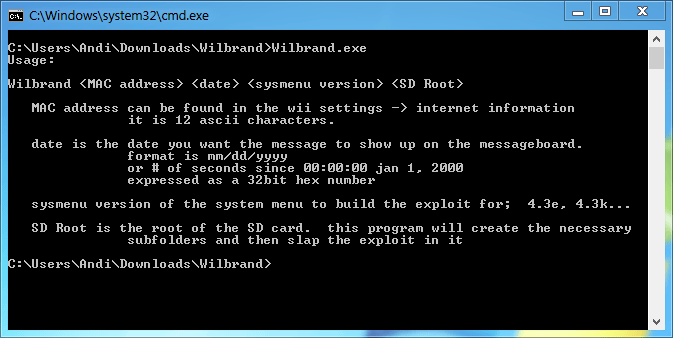
This is a cli program. Here is the usage:
Wilbrand <MAC address> <date> <sysmenu version> <SD Root>
| Term | Definition |
|---|---|
| MAC Address | The wireless MAC address of the wii. you can get this from the internet settings, or if those are inaccessible for whatever reason, many routers will display it. It may contain dashes, colons, or spaces, but should be 12 hex characters when these extra characters are removed. |
| Date | this is the date you want the message to show up under in the message board. It should be within the range of 2000 - 2035. Accepted formats are mm/dd/yyyy or in a 32bit hex representation of the number of seconds since 00:00 Jan, 01 2000. NOTE The System menu is triggered to load messages from the SD card when you scroll across days. So if you build the message for the current day, you will have to scroll to a different day and then back again to trigger the loading of it. |
| SysmenuVersion | This is the version of the System menu to build the exploit for. It can be read in the first page under Wii settings. Accepted formats are 3.2u, 32u, 3.2U, and 32U. Accepted versions are any official, publicly released version from 3.0 - 4.3. |
| SD Root | This is the base folder where you would like the message created. The design of the cdb archive uses about 13 subfolders to store files. This program will use the given folder and create the necessary folder structure and then place the exploit message in its place. |
Examples:
./Wilbrand 001122334455 10/25/2011 3.2u /media/sdcard
./Wilbrand 00-11-22-33-44-55 163a09c4 43U /media/sdcard
./Wilbrand '00 11 22 33 44 55' 163a09c4 4.3K F:
You need to use an SD card that is supported by your system menu version. To test this, go to the data management or SD card menu and try to use the SD card.
It will tell you if it can't be used. Once you have run this program, and have the exploit message on your SD card, you need some homebrew to load. This one works pretty well. Save the homebrew as SD:/boot.elf.
Then stick the SD card in your Wii, start it up, go to the message board, and then scroll to the day that the exploit was built for. It should be easily identifiable as it will be the best looking envelope there. Click it and watch the magic happen.
Screenshots
FAQ
Q. I can't run the program./Wilbrand just gives me errors and doesn't build the exploit.
Read and re-read the usage instructions. Google how to use a cli program.
Q. I don't see the incredibly cool image.
Double check that you are looking at the date you gave to wilbrand when building the exploit.
Make sure the system menu can access your SD card.
Make sure you gave the correct WIRELESS MAC address to the program.
Q. When I click the message, it freezes.
You gave the wrong system menu version when building the exploit message.
Q. I click the message and I get a black screen with white text flying by over and over.
Make sure you have SD:/boot.elf. Try with a different SD card. Apparently this SD code doesn't like some cards.
Changelog
3.0
- Initial public release.
Credits
Authors:
- Hackmii team - Savezelda's loader was used as a starting point for the payload.
- Paul E. Jones - sha1 code.
- Mike Scott - AES code.
- Others - there is some misc code involved (such as wbe32()) that was takes from various open-source projects which was very nice to have, but I'm sure I couldn't name all occurances and credit all authors appropriately.
- giantpune - finding the initial bug [WOOHOO!], dumping and debugging 32 version of the system menu to find the offsets, pretty much everything else involved.
External links
- GitHub - https://github.com/giantpune/mailboxbomb
- Wiidatabase - https://wiidatabase.de/downloads/exploits/wilbrand/
