More actions
m (Text replacement - "GameBrew!" to "GameBrew") |
No edit summary |
||
| (10 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
|title=Vita Homebrew PC Tools (PC Utilities) - GameBrew | |title=Vita Homebrew PC Tools (PC Utilities) - GameBrew | ||
|title_mode=append | |title_mode=append | ||
|image= | |image=psvpfstoolsvita2.png | ||
|image_alt=psvpfstools | |image_alt=psvpfstools | ||
}} | }} | ||
{{Infobox Vita Homebrews | {{Infobox Vita Homebrews | ||
|title=psvpfstools | |title=psvpfstools | ||
|image= | |image=psvpfstoolsvita2.png | ||
|description=PFS | |description=Tools for decrypting PS Vita PFS filesystem. | ||
|author=motoharu | |author=motoharu | ||
|lastupdated=2018/01/27 | |lastupdated=2018/01/27 | ||
| Line 15: | Line 15: | ||
|license=Mixed | |license=Mixed | ||
|download=https://dlhb.gamebrew.org/vitahomebrews/psvpfstoolsvita.7z | |download=https://dlhb.gamebrew.org/vitahomebrews/psvpfstoolsvita.7z | ||
|website= | |website=https://github.com/motoharu-gosuto/psvpfstools | ||
|source=https://github.com/motoharu-gosuto/psvpfstools | |source=https://github.com/motoharu-gosuto/psvpfstools | ||
}} | }} | ||
psvpfstools is a set of tools that allows to decrypt PFS filesystem layer of PS Vita. | |||
In the past the only good way to do this was to mount PFS for example in | In the past the only good way to do this was to mount PFS for example in [[VitaShell]] and let PS Vita to decrypt the files. | ||
However this tool is a completely new standalone approach that does not require you to have PS Vita. | However this tool is a completely new standalone approach that does not require you to have PS Vita. | ||
All decryption is done directly on the PC. | All decryption is done directly on the PC. | ||
== Public F00D service == | ==User guide== | ||
=== Public F00D service === | |||
PFS tools were designed in such a way that implementation of F00D crypto layer can be provided separately. | PFS tools were designed in such a way that implementation of F00D crypto layer can be provided separately. | ||
Currently you can use a service url located at: http://cma.henkaku.xyz | Currently you can use a service url located at: http://cma.henkaku.xyz | ||
=== Why do I need F00D service | ===Why do I need F00D service=== | ||
The only purpose of F00D service is to take the given key, encrypt it and give it back. F00D service | The only purpose of F00D service is to take the given key, encrypt it and give it back. F00D service does not decrypt PFS. To those that are curious - service does not use PS Vita as well. | ||
Typically during decryption process service is called only once to encrypt klicensee that is extracted from zRIF string if you are decrypting gamedata or addcont (unicv.db format). Service is called once to encrypt key that is extracted from sealedkey file if you are decrypting savedata, trophies, appmeta, addcont root (icv.db format). | Typically during decryption process service is called only once to encrypt klicensee that is extracted from zRIF string if you are decrypting gamedata or addcont (unicv.db format). Service is called once to encrypt key that is extracted from sealedkey file if you are decrypting savedata, trophies, appmeta, addcont root (icv.db format). | ||
| Line 56: | Line 57: | ||
* json files | * json files | ||
=== Format of flat files === | |||
* titleid (only for information, not used) | * titleid (only for information, not used) | ||
* klicensee | * klicensee | ||
| Line 65: | Line 66: | ||
PCSE22222 22222222222222222222222222222222 22222222222222222222222222222222</pre> | PCSE22222 22222222222222222222222222222222 22222222222222222222222222222222</pre> | ||
=== Format of json files === | |||
<pre>{ | <pre>{ | ||
"PCSE00000" : | "PCSE00000" : | ||
| Line 85: | Line 86: | ||
</pre> | </pre> | ||
== What | === What can be decrypted === | ||
Tool now supports both icv.db and unicv.db formats. | Tool now supports both icv.db and unicv.db formats. | ||
| Line 96: | Line 97: | ||
In case of specific problems please refer to the next section. | In case of specific problems please refer to the next section. | ||
== | ===How to use=== | ||
When decrypting unicv.db: use <code>-k</code> or <code>-z</code> option to provide klicensee data. | |||
When decrypting icv.db: dont use <code>-k</code> and <code>-z</code>. klicensee data will be taken automatically from sealedkey file. | |||
Options: | |||
-h [ --help ] Show help. | |||
-i [ --title_id_src ] arg Source directory that contains the application. Like PCSC00000. | |||
-o [ --title_id_dst ] arg Destination directory where everything will be unpacked. Like PCSC00000_dec. | |||
-k [ --klicensee ] arg klicensee hex coded string. Like 00112233445566778899AABBCCDDEEFF. | |||
-z [ --zRIF ] arg zRIF string. | |||
-f [ --f00d_url ] arg Url of F00D service. | |||
-c [ --f00d_cache ] arg Path to flat or json file with F00D cache. | |||
==Screenshots== | |||
https://dlhb.gamebrew.org/vitahomebrews/psvpfstoolsvita3.png | |||
== Known issues == | |||
https://github.com/motoharu-gosuto/psvpfstools/issues | https://github.com/motoharu-gosuto/psvpfstools/issues | ||
PFS tools are still under developement and testing. | |||
If you find bugs or have problems with decrypting specific data please consider leaving a report in the issues page. | |||
==Changelog== | ==Changelog== | ||
''' | '''v2.0''' | ||
*Support of icv.db format (savedata, trophies etc) | *Support of icv.db format (savedata, trophies etc). | ||
*Keystone and Sealedkey parsing and Keystone sanity check | *Keystone and Sealedkey parsing and Keystone sanity check. | ||
*Complete rewrite of unicv.db parser (to accomodate icv.db) | *Complete rewrite of unicv.db parser (to accomodate icv.db). | ||
*Support of Merkle trees (related to icv.db) | *Support of Merkle trees (related to icv.db). | ||
*Cleanup and improvement of crypto engine (more reversing done) | *Cleanup and improvement of crypto engine (more reversing done). | ||
*Improvement of different places in the code that had unknown behavior (reversing) | *Improvement of different places in the code that had unknown behavior (reversing). | ||
*Bug fixes that were in previous versions | *Bug fixes that were in previous versions. | ||
==Special thanks | ==Credits== | ||
Special thanks: | |||
* Proxima. For initial docs on DMAC5, contributing code for keystone and sealedkey checks, providing F00D service and help with crypto theory, advising on libtomcrypt. | * Proxima. For initial docs on DMAC5, contributing code for keystone and sealedkey checks, providing F00D service and help with crypto theory, advising on libtomcrypt. | ||
* St4rk, weaknespase and everyone involved in PkgDecrypt. For zRIF string decode/inflate code. | * St4rk, weaknespase and everyone involved in PkgDecrypt. For zRIF string decode/inflate code. | ||
| Line 123: | Line 140: | ||
* CelesteBlue for indicating possibility of sealedkey usage as local key. | * CelesteBlue for indicating possibility of sealedkey usage as local key. | ||
* tomazzz369 for testing and providing XP build | * tomazzz369 for testing and providing XP build | ||
* MRGhidini for testing and integration into [[Psvimgtools Easy Frontend Vita]] | * MRGhidini for testing and integration into [[Psvimgtools Easy Frontend Vita]]. | ||
* Chris Venter. For libb64. Integrated as source. | * Chris Venter. For libb64. Integrated as source.. | ||
== External links == | == External links == | ||
* | * GitHub - https://github.com/motoharu-gosuto/psvpfstools | ||
* VitaDB - https://vitadb.rinnegatamante.it/#/info/362 | * VitaDB - https://vitadb.rinnegatamante.it/#/info/362 | ||
Latest revision as of 00:51, 23 Ocak 2023
| psvpfstools | |
|---|---|
 | |
| General | |
| Author | motoharu |
| Type | PC Utilities |
| Version | 2.0 |
| License | Mixed |
| Last Updated | 2018/01/27 |
| Links | |
| Download | |
| Website | |
| Source | |
psvpfstools is a set of tools that allows to decrypt PFS filesystem layer of PS Vita.
In the past the only good way to do this was to mount PFS for example in VitaShell and let PS Vita to decrypt the files.
However this tool is a completely new standalone approach that does not require you to have PS Vita.
All decryption is done directly on the PC.
User guide
Public F00D service
PFS tools were designed in such a way that implementation of F00D crypto layer can be provided separately.
Currently you can use a service url located at: http://cma.henkaku.xyz
Why do I need F00D service
The only purpose of F00D service is to take the given key, encrypt it and give it back. F00D service does not decrypt PFS. To those that are curious - service does not use PS Vita as well.
Typically during decryption process service is called only once to encrypt klicensee that is extracted from zRIF string if you are decrypting gamedata or addcont (unicv.db format). Service is called once to encrypt key that is extracted from sealedkey file if you are decrypting savedata, trophies, appmeta, addcont root (icv.db format).
On Vita - there are 3 hardware implementations of crypto functions:
- Use key - you have a freedom of giving the key to crypto function and key is used directly.
- Use slot_id - you have to set the key into specific slot. Then by specifying key_id you instruct F00D to encrypt your key with specific key from F00D. Encrypted key is then used in crypto function of your choice.
- Use key_id - you give the key and specify key_id. Your key is then encrypted with specific key from F00D. Encrypted key is then put into one of the slots in default range. After that encrypted key can be used in crypto function of your choice.
You can read more about crypto functions here: https://wiki.henkaku.xyz/vita/SceSblSsMgr#SceSblSsMgrForDriver
F00D service cache
Instead of using F00D service directly it is now possible to use a cache file that is created beforehand.
To use it pass path to the file with --f00d_cache option.
When using --f00d_url option you will get an F00D cache output that you can copy to a cache file.
Two types of files are allowed:
- flat files with delimiters like " ", "\t", ","
- json files
Format of flat files
- titleid (only for information, not used)
- klicensee
- encrypted key
PCSE00000 00000000000000000000000000000000 00000000000000000000000000000000 PCSE11111 11111111111111111111111111111111 11111111111111111111111111111111 PCSE22222 22222222222222222222222222222222 22222222222222222222222222222222
Format of json files
{
"PCSE00000" :
{
"key" : "00000000000000000000000000000000",
"value" : "00000000000000000000000000000000"
},
"PCSE11111" :
{
"key" : "11111111111111111111111111111111",
"value" : "11111111111111111111111111111111"
},
"PCSE22222" :
{
"key" : "22222222222222222222222222222222",
"value" : "22222222222222222222222222222222"
}
}
What can be decrypted
Tool now supports both icv.db and unicv.db formats.
Which means that it can decrypt gamedata, addcont, savedata, trophies, appmeta, addcont root.
In theory everything that is PFS encrypted can be decrypted.
The tool was tested in all scenarios listed above, including 3.61+ games.
In case of specific problems please refer to the next section.
How to use
When decrypting unicv.db: use -k or -z option to provide klicensee data.
When decrypting icv.db: dont use -k and -z. klicensee data will be taken automatically from sealedkey file.
Options:
-h [ --help ] Show help. -i [ --title_id_src ] arg Source directory that contains the application. Like PCSC00000. -o [ --title_id_dst ] arg Destination directory where everything will be unpacked. Like PCSC00000_dec. -k [ --klicensee ] arg klicensee hex coded string. Like 00112233445566778899AABBCCDDEEFF. -z [ --zRIF ] arg zRIF string. -f [ --f00d_url ] arg Url of F00D service. -c [ --f00d_cache ] arg Path to flat or json file with F00D cache.
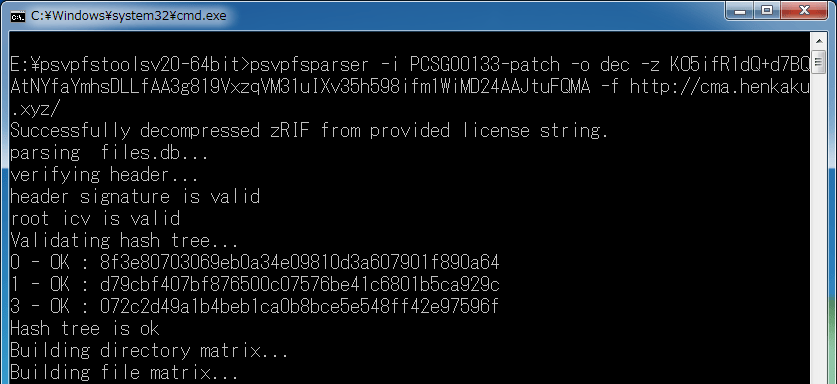
Screenshots
Known issues
https://github.com/motoharu-gosuto/psvpfstools/issues
PFS tools are still under developement and testing.
If you find bugs or have problems with decrypting specific data please consider leaving a report in the issues page.
Changelog
v2.0
- Support of icv.db format (savedata, trophies etc).
- Keystone and Sealedkey parsing and Keystone sanity check.
- Complete rewrite of unicv.db parser (to accomodate icv.db).
- Support of Merkle trees (related to icv.db).
- Cleanup and improvement of crypto engine (more reversing done).
- Improvement of different places in the code that had unknown behavior (reversing).
- Bug fixes that were in previous versions.
Credits
Special thanks:
- Proxima. For initial docs on DMAC5, contributing code for keystone and sealedkey checks, providing F00D service and help with crypto theory, advising on libtomcrypt.
- St4rk, weaknespase and everyone involved in PkgDecrypt. For zRIF string decode/inflate code.
- devnoname120 for hmac_sha256 crypto primitives that were used in initial implementation.
- SilicaAndPina for pointing at trophy and savedata pfs.
- CelesteBlue for indicating possibility of sealedkey usage as local key.
- tomazzz369 for testing and providing XP build
- MRGhidini for testing and integration into Psvimgtools Easy Frontend Vita.
- Chris Venter. For libb64. Integrated as source..
