More actions
No edit summary |
No edit summary |
||
| (7 intermediate revisions by the same user not shown) | |||
| Line 5: | Line 5: | ||
|author=Nicholas Scheltema | |author=Nicholas Scheltema | ||
|lastupdated=2007/03/04 | |lastupdated=2007/03/04 | ||
|type=Role | |type=Role Playing | ||
|version=1.2 | |version=1.2 | ||
|license=Mixed | |license=Mixed | ||
|download=https://dlhb.gamebrew.org/gbahomebrews/ | |download=https://dlhb.gamebrew.org/gbahomebrews/matrix_runner_04.03.2007_gba.zip | ||
|website=https://pdroms.de/files/nintendo-gameboyadvance-gba/matrix-runner-04-03-2007 | |website=https://pdroms.de/files/nintendo-gameboyadvance-gba/matrix-runner-04-03-2007 | ||
}} | }} | ||
| Line 17: | Line 17: | ||
|image_alt=Matrix Runner | |image_alt=Matrix Runner | ||
}} | }} | ||
Matrix Runner is a role playing homebrew game inspired by William Gibson's Neuromancer book and it's sequels with a bit of influence from the likewise inspired RPG, Shadowrun. | Matrix Runner is a role playing homebrew game inspired by William Gibson's Neuromancer book and it's sequels with a bit of influence from the likewise inspired RPG, Shadowrun. | ||
| Line 130: | Line 129: | ||
https://dlhb.gamebrew.org/gbahomebrews/matrixrunner3.png | https://dlhb.gamebrew.org/gbahomebrews/matrixrunner3.png | ||
https://dlhb.gamebrew.org/gbahomebrews/matrixrunner4.png | https://dlhb.gamebrew.org/gbahomebrews/matrixrunner4.png | ||
<!--BEGIN Online Emulator Section--> | |||
==Online emulator== | |||
{{EmulatorJS Main | |||
|width=480px | |||
|height=400px | |||
|EJS_backgroundBlur=false | |||
|EJS_backgroundImage=https://www.gamebrew.org/images/1/1f/Matrixrunner02.png | |||
|EJS_core=gba | |||
|EJS_gameName=Matrix Runner | |||
|EJS_gameUrl=https://dlhb.gamebrew.org/onlineemulators/gba/matrix_runner_04.03.2007_gba.7z | |||
}} | |||
{{GBA Control Settings}} | |||
<!--END Online Emulator Section--> | |||
==Compatibility== | ==Compatibility== | ||
This game was untested on the real hardware, but it worked 100% on VisualBoyAdvance. | This game was untested on the real hardware, but it worked 100% on VisualBoyAdvance. | ||
| Line 139: | Line 150: | ||
* PDRoms - https://pdroms.de/files/nintendo-gameboyadvance-gba/matrix-runner-04-03-2007 | * PDRoms - https://pdroms.de/files/nintendo-gameboyadvance-gba/matrix-runner-04-03-2007 | ||
[[Category: | [[Category:PDRoms Coding Competition 3.666]] | ||
Latest revision as of 04:32, 20 August 2024
| Matrix Runner | |
|---|---|
 | |
| General | |
| Author | Nicholas Scheltema |
| Type | Role Playing |
| Version | 1.2 |
| License | Mixed |
| Last Updated | 2007/03/04 |
| Links | |
| Download | |
| Website | |
Matrix Runner is a role playing homebrew game inspired by William Gibson's Neuromancer book and it's sequels with a bit of influence from the likewise inspired RPG, Shadowrun.
It was presented in the PDRoms Coding Competition #3.666 (1st place).
User guide
You play the role of a hacker in the future, a "decker", jacking into the global computer network "The Matrix" with a direct brain link that enables you to experience the computer network as a virtual reality.
How to play
For each network in the game there is a contract for a particular task to be done. This could be stealing files from data stores, using devices through i/o ports or crashing the CPU. You get paid when you accomplish this task; the higher the network number, the more you get paid. But the higher network numbers are also more difficult and dangerous to attack.
When you start the game you must select the network you want to attack. The alert level beneath the network will indicate whether or not you can enter the network; green means you can, red means you cannot.
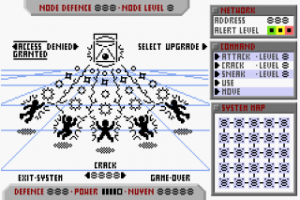
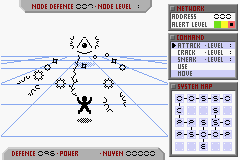
Once you've selected a network, the system map will draw the layout of the network. Your position in indicated by the flashing node, your target node is highlighted with four dots around it. Each square represents a possible node location, and the lines between them indicate paths between the nodes. Each node symbol in the squares indicate what the node is:
C (CPU, the central core of the network):
- Notes: You can travel to anywhere in the network from here, bypassing active security.
- Use command: Crashes the network, automatically jacking you out.
S (Store, a data storage node on the network):
- Notes: May contain other data of worth.
- Use command: retrieve files.
P (Port, an interface to an external device):
- Use command: activate the port.
E (Entrance / exit):
- Notes: Moving to this node will cause you to jack out of the system.
O (Unused node):
- Notes: Have no security systems.
Interact with the node
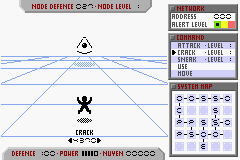
When interacting with a node, the main display area lights up.
- You will see the node you are interacting in the centre of the display and your avatar near the bottom.
- On the right hand side is the command list.
- At the bottom left is the player's defence, attack power and nuyen amount.
- At the top left is the node's statistics, the node defence indicates the security system's integrity and the node level indicates how powerful the system security is.
The available commands include Attack, Crack, Sneak, Use and Move.
Attack:
- Damage the security system, reducing the node defence amount.
- Upside - Guaranteed to succeed eventually.
- Downside - Red alert sounded.
Crack:
- Try to penetrate defences using algorithms to generate passcodes.
- Upside - Disables security on success.
- Downside - Moderate success rate.
Sneak:
- Try to disguise your signature on the network as something mundane so the system ignores you.
- Upside - Temporarily bypass system security.
- Downside - Security is not disabled.
Use:
- Access the node's functionality, see the node list above for details.
- The node's security must be disabled for this to work.
Move:
- Leave this node, this will take you back to the system map to move around.
The level of the program vs the level of the node determines the success rate of the command. A sphere in the middle of the node indicates the security is still active, when the node's defence reaches zero the security is disabled. Once you've been to a node, it is easier to return, possibly even bypassing nodes you snuck passed before.
The network has an alert level, which is indicated beneath the network number and can be either green, yellow or red.
- Repeatedly failing to crack, sneak or use a node will make the system suspicious and it will raise the alert level.
- Attacking a node will set the whole system to red alert instantly.
- Once the system is in red alert, attempts to crack or sneak will fail, nor will you be able to leave a node with active security.
- All security in a network is reset when you re-enter it after leaving it.
In red alert mode, all the system nodes' security will attack you, the higher the node level, the faster and more damaging the attacks are.
- You must dodge the attacks coming towards you by moving your avatar.
- Every hit damages your defences, and when your defences hit zero, its game-over and your brain gets fried!
- When you are game over, the number of objectives you completed are displayed at the bottom of the screen.
- Your only option in red alert mode is to attack. The higher the level of the attack program, the faster it constructs attacks and the more damage it does.
Once you've removed the defences and completed the objective, you must make your way back to the exit node to jack out. If you crash the CPU, you jack out automatically. You cannot re-enter a network once you've completed its objective, the alert level will be set to red permanently and refuse all incoming connections.
Whenever you leave a network, you get the opportunity to buy upgrades for your programs.
- The higher the level your program, the more effective it is.
- The cost of each upgrade to the next level is the current level of the program multiplied by 1000 nuyen.
- After the upgrade menu, you return to the network select mode to choose your next target.
If you can complete all 256 available networks, you win and earn the title of being elite.
Strategy
The basic strategy is to avoid setting off alarms and red alert while trying to reach the objective.
You should try to crack and sneak your way through the system.
Log into networks, raid non-objective datastores and log out again to save up for upgrades.
You should only attack if red alert is sounded or the defences are way too high to crack or sneak by.
Note: All the networks are procedurally generated, so they will be the same every time you play the game. It is possible to learn or even map the game.
Controls
Up/Down - Select network number and commands
Left/Right - Move your avatar in the matrix
A - Action, Interact with node, Start game from the startup demo mode (menu)
B - Cancel
On the system map:
D-Pad - Move your position in the network
Screenshots
Online emulator
| Game Boy Advance | Keyboard |
|---|---|
Compatibility
This game was untested on the real hardware, but it worked 100% on VisualBoyAdvance.
If you are going to try it on the real thing, you will need to GBAFIX the rom header information.
