More actions
No edit summary |
m (Text replacement - "Category:3DS homebrew system tools" to "") |
||
| (6 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
{{Infobox 3DS Homebrews | {{Infobox 3DS Homebrews | ||
|title=Boot9strap | |title=Boot9strap | ||
|image= | |image=Boot9strap2.png | ||
|description=Boot9/Boot11 code execution. | |description=Boot9/Boot11 code execution. | ||
|author=SciresM, Hedgeberg | |author=SciresM, Hedgeberg | ||
|lastupdated= | |lastupdated=2022/05/23 | ||
|type=System Tools | |type=System Tools | ||
|version=1. | |version=1.4 | ||
|license=GPL-3.0 | |license=GPL-3.0 | ||
|download=https://dlhb.gamebrew.org/3dshomebrews/ | |download=https://dlhb.gamebrew.org/3dshomebrews/boot9strap.7z | ||
|website=https://github.com/SciresM/boot9strap | |website=https://github.com/SciresM/boot9strap | ||
|source=https://github.com/SciresM/boot9strap | |source=https://github.com/SciresM/boot9strap | ||
| Line 14: | Line 14: | ||
Boot9strap (B9S) is a modified firmware that makes use of sighax and a vulnerability in the console's NDMA engine to gain code execution on the ARM9 BootROM (Boot9) and load a payload (boot.firm) from the SD card. It uses a modified version the ARM9 payload loader of [[Luma3DS]]. The software can also dump the console-specific OTP and BootROMs. | Boot9strap (B9S) is a modified firmware that makes use of sighax and a vulnerability in the console's NDMA engine to gain code execution on the ARM9 BootROM (Boot9) and load a payload (boot.firm) from the SD card. It uses a modified version the ARM9 payload loader of [[Luma3DS]]. The software can also dump the console-specific OTP and BootROMs. | ||
B9S is a bootrom exploit that runs a lot earlier in the boot process in comparison to Armloader9hax (A9LH), allowing access to new system files that A9LH didn't, as well as adding better brick protection, and update protection, because it's unpatchable without a hardware revision (it is also worth noting that B9S uses .firm files instead of .bin files for payloads). B9S has effectively replaced AL9H, and if you use Luma3DS and would like to still be supported with updates, you have to switch to B9S. | |||
For more technical details, refer to the presentation [https://sciresm.github.io/33-and-a-half-c3 here]. | For more technical details, refer to the presentation [https://sciresm.github.io/33-and-a-half-c3 here]. | ||
==Installation== | ==Installation== | ||
Install via [[SafeB9SInstaller 3DS|SafeB9SInstaller]]. | Install via [[SafeB9SInstaller 3DS|SafeB9SInstaller]], or follow the [http://3ds.guide community guide]. | ||
Launches boot.firm off of the SD card or CTRNAND. | Launches boot.firm off of the SD card or CTRNAND. | ||
Hold Start+Select+X on boot to dump the bootroms/your OTP. | Hold Start+Select+X on boot to dump the bootroms/your OTP. | ||
==Changelog== | |||
'''v1.4''' | |||
*Boots around 0.25s to 0.4s faster. | |||
*Size halved, now under 16KB. | |||
*If the ntrboot combo (X+Start+Select) is held, or if either FIRM file is corrupt, the notification LED will display the following: | |||
**SD FIRM successfully loaded: green. | |||
**SD FIRM missing, CTRNAND FIRM successfully loaded: yellow. | |||
**SD FIRM corrupt, CTRNAND FIRM successfully loaded: orange. | |||
**SD FIRM missing, CTRNAND FIRM also missing: white. | |||
**SD FIRM missing, CTRNAND FIRM corrupt: magenta. | |||
**SD FIRM corrupt, CTRNAND FIRM also corrupt: red. | |||
**in addition to the above, the LED will blink if it is actually a ntrboot boot. | |||
*Ability to dump boot9/boot11/otp removed (recent Luma commits auto-backup otp.bin anyway). It's also how such improvments could be made in the first place | |||
'''v1.3''' | |||
* Removed some unnecessary padding to make B9S FIRMs smaller (they now size about 30 KiB, and thus can support NTRboot targets with smaller flashes). | |||
* Updated the filesystem library used by the stage 2 loader. | |||
* Added additional delay following ntrboot to allow for more time to hold a button-combination for the loaded boot.firm. | |||
'''v1.2''' | |||
* Fixes some critical bugs due to rushed 1.0 release. | |||
* When requested, framebuffers are now passed via argv rather than using legacy cakebrah buffers. | |||
* The loader now runs from a stub in itcm -- this lifts restrictions on boot.firms' ability to load. | |||
* By setting a bit in the firm header, execution can be handed over pre bootrom-lockout. | |||
* Fixes a compatibility issue in 1.1 where some payloads would respond poorly to ntrboot. | |||
* In a similar vein, dumping bootrom via held key combination shut the device down in 1.1. It now waits for the user to let go of the keys before resuming boot. | |||
* Further improvements to overall system stability and other minor adjustments have been made to enhance the user experience. | |||
'''v1.1''' | |||
* Fixes some critical bugs due to rushed 1.0 release. | |||
* When requested, framebuffers are now passed via argv rather than using legacy cakebrah buffers. | |||
* The loader now runs from a stub in itcm -- this lifts restrictions on boot.firms' ability to load. | |||
* By setting a bit in the firm header, execution can be handed over pre bootrom-lockout. | |||
* Further improvements to overall system stability and other minor adjustments have been made to enhance the user experience. | |||
==Credits== | ==Credits== | ||
| Line 31: | Line 66: | ||
==External links== | ==External links== | ||
* Sighax and Boot9strap Presentation - https://sciresm.github.io/33-and-a-half-c3 | |||
* GitHub - https://github.com/SciresM/boot9strap | * GitHub - https://github.com/SciresM/boot9strap | ||
* 3DS Hacks Guide - http://3ds.guide | |||
Latest revision as of 05:18, 6 Mayıs 2024
| Boot9strap | |
|---|---|
 | |
| General | |
| Author | SciresM, Hedgeberg |
| Type | System Tools |
| Version | 1.4 |
| License | GPL-3.0 |
| Last Updated | 2022/05/23 |
| Links | |
| Download | |
| Website | |
| Source | |
Boot9strap (B9S) is a modified firmware that makes use of sighax and a vulnerability in the console's NDMA engine to gain code execution on the ARM9 BootROM (Boot9) and load a payload (boot.firm) from the SD card. It uses a modified version the ARM9 payload loader of Luma3DS. The software can also dump the console-specific OTP and BootROMs.
B9S is a bootrom exploit that runs a lot earlier in the boot process in comparison to Armloader9hax (A9LH), allowing access to new system files that A9LH didn't, as well as adding better brick protection, and update protection, because it's unpatchable without a hardware revision (it is also worth noting that B9S uses .firm files instead of .bin files for payloads). B9S has effectively replaced AL9H, and if you use Luma3DS and would like to still be supported with updates, you have to switch to B9S.
For more technical details, refer to the presentation here.
Installation
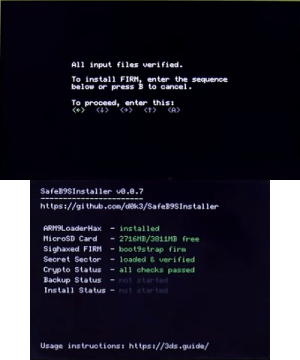
Install via SafeB9SInstaller, or follow the community guide.
Launches boot.firm off of the SD card or CTRNAND.
Hold Start+Select+X on boot to dump the bootroms/your OTP.
Changelog
v1.4
- Boots around 0.25s to 0.4s faster.
- Size halved, now under 16KB.
- If the ntrboot combo (X+Start+Select) is held, or if either FIRM file is corrupt, the notification LED will display the following:
- SD FIRM successfully loaded: green.
- SD FIRM missing, CTRNAND FIRM successfully loaded: yellow.
- SD FIRM corrupt, CTRNAND FIRM successfully loaded: orange.
- SD FIRM missing, CTRNAND FIRM also missing: white.
- SD FIRM missing, CTRNAND FIRM corrupt: magenta.
- SD FIRM corrupt, CTRNAND FIRM also corrupt: red.
- in addition to the above, the LED will blink if it is actually a ntrboot boot.
- Ability to dump boot9/boot11/otp removed (recent Luma commits auto-backup otp.bin anyway). It's also how such improvments could be made in the first place
v1.3
- Removed some unnecessary padding to make B9S FIRMs smaller (they now size about 30 KiB, and thus can support NTRboot targets with smaller flashes).
- Updated the filesystem library used by the stage 2 loader.
- Added additional delay following ntrboot to allow for more time to hold a button-combination for the loaded boot.firm.
v1.2
- Fixes some critical bugs due to rushed 1.0 release.
- When requested, framebuffers are now passed via argv rather than using legacy cakebrah buffers.
- The loader now runs from a stub in itcm -- this lifts restrictions on boot.firms' ability to load.
- By setting a bit in the firm header, execution can be handed over pre bootrom-lockout.
- Fixes a compatibility issue in 1.1 where some payloads would respond poorly to ntrboot.
- In a similar vein, dumping bootrom via held key combination shut the device down in 1.1. It now waits for the user to let go of the keys before resuming boot.
- Further improvements to overall system stability and other minor adjustments have been made to enhance the user experience.
v1.1
- Fixes some critical bugs due to rushed 1.0 release.
- When requested, framebuffers are now passed via argv rather than using legacy cakebrah buffers.
- The loader now runs from a stub in itcm -- this lifts restrictions on boot.firms' ability to load.
- By setting a bit in the firm header, execution can be handed over pre bootrom-lockout.
- Further improvements to overall system stability and other minor adjustments have been made to enhance the user experience.
Credits
External links
- Sighax and Boot9strap Presentation - https://sciresm.github.io/33-and-a-half-c3
- GitHub - https://github.com/SciresM/boot9strap
- 3DS Hacks Guide - http://3ds.guide
