More actions
No edit summary |
|||
| Line 44: | Line 44: | ||
==Screenshots== | ==Screenshots== | ||
{| | {| style="width: 80%;" | ||
|- | |- | ||
|'''Main''' | |'''Main''' | ||
Latest revision as of 12:34, 29 Mayıs 2023
| Incognito_RCM | |
|---|---|
 | |
| General | |
| Author | jimzrt |
| Type | System Tools |
| Version | 0.6.1 |
| License | GPL-2.0 |
| Last Updated | 2020/01/06 |
| Links | |
| Download | |
| Website | |
| Source | |
| This application has been obsoleted by one or more applications that serve the same purpose, but are more stable or maintained. |
Incognito_RCM is a bare metal Nintendo Switch payload that derives encryption keys for de- and encrypting PRODINFO partition (sysnand and emummc) and wiping personal information from your Nintendo Switch as to go online while worrying slightly less about a ban. It has a builtin backup and restore functionality.
It is heavily based on Lockpick RCM and takes inspiration from incognito.
Note: If you have Atmosphere, it's recommended that you configure exosphere.ini to conceal your serial instead.
Features
- Wipe personal information on sysnand/emunand.
- Backup prodinfo from sysnand/emunand.
- Restore prodinfo to sysnand/emunand.
User guide
Note: This project is in early stage, so have a nand backup.
Launch Incoginito_RCM.bin using your favorite payload injector.
Use menu to make a backup (will be written to sd:/prodinfo_sysnand.bin and sd:/prodinfo_emunand.bin respectively).
Choose either Incognito (sysNAND) or Incognito (emuMMC) to wipe personal information.
If you ever want to revert, choose restore menu points.
Notes
This application does not remove all personal information from your Switch, and should not be treated as a true preventative measure against getting banned.
Always have a NAND backup. The author is not responsible for any bricks or bans. Use at your own risk, as this is an experimental program.
This application backs up your PRODINFO to the SD card. You should keep this backup in a more secure location, and not leave it on the SD card where it could be subject to corruption or be read by malicious applications.
Screenshots
| Main | Incognito |
|
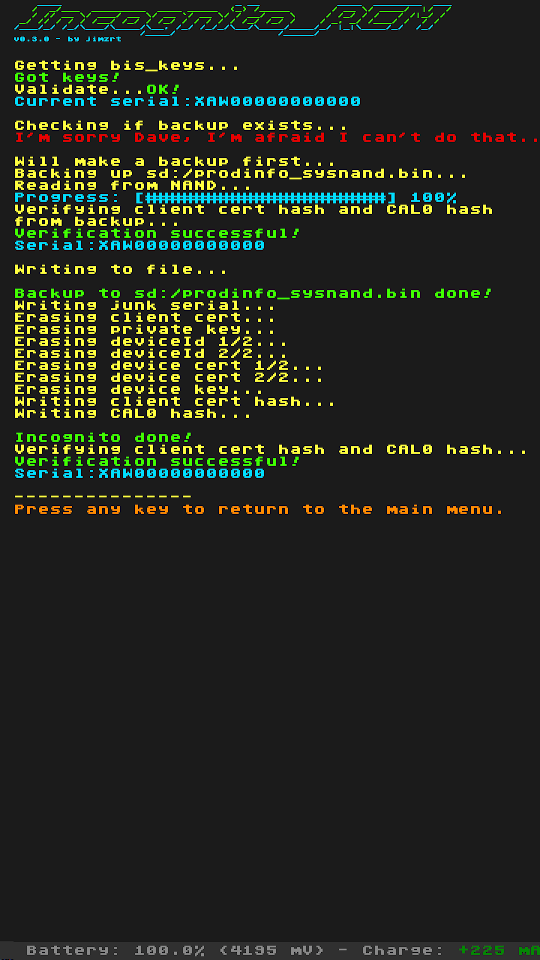
|
| Backup | Restore |
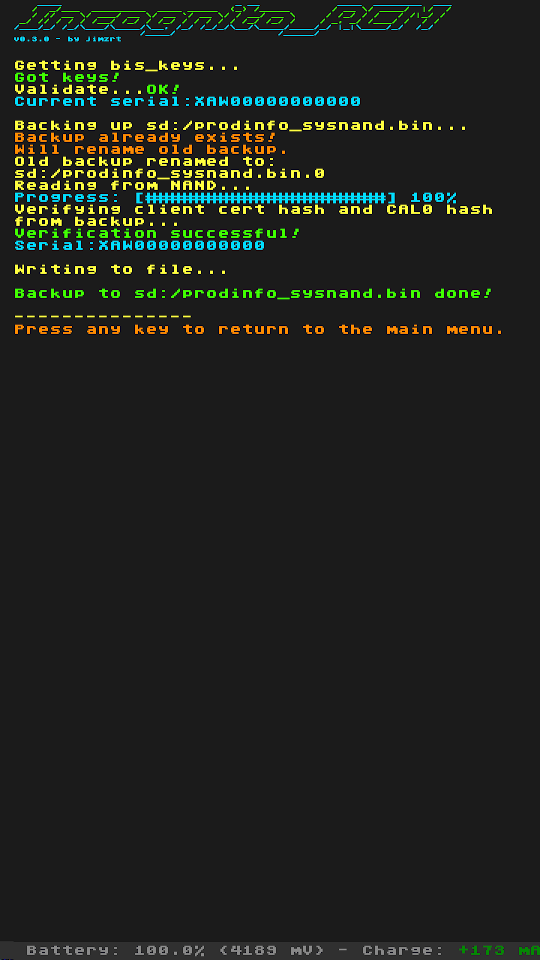
|
|
Compatibility
This has only been tested by the author on firmware 8.1.0.
Known issues
Chainloading from SX will hang immediately due to quirks in their hwinit code, please launch payload directly.
Changelog
v0.6.1 2020/01/06
- Bugfix: write to emummc instead of sdmmc.
v0.6.0 2020/01/05
- Incorporate hekate & lockpick_rcm changes.
- Reboot to payload.
v0.5.1 2020/01/03
- Support for firmware 9.1.0.
v0.4.0 2019/10/26
- Adopt lockpick_rcm and hekate changes (includes fixing of possible bugs and better resource management).
- Reduced payload size.
- Use tui progressbar.
v0.3.0 2019/10/08
- More error handling.
- Backup validation when reading and writing.
- Retry up to 5 times when reading and writing before aborting.
v0.2.0 2019/10/07
- More validation.
- Code cleanup and refactoring.
v0.1.0 2019/10/05
- Much faster read and write speed (not sector by sector anymore).
- Much more validation and verification (still not perfect).
- More error handling (still not perfect).
- Backups aren't overwritten, old backups are renamed.
- Check for backup before applying incognito.
- Auto-restore backup if something goes wrong.
- As always, have a NAND backup ready!
v0.0.2 2019/10/04
- Removed external libraries and better handling of reading big chunks of memory.
Credits
Massive Thanks to CTCaer, shchmue and blawar.
