More actions
(Created page with "{{Infobox Switch Homebrews |title=BiskeyDump |image=biskeydumpswitch.png |description=fusee payload that dumps your BIS keys. |author=rajkosto |lastupdated=2019/06/22 |type=PC Utilities |version=9 |license=GPL-2.0 |download=https://dlhb.gamebrew.org/switchhomebrews/biskeydumpswitch.7z |website=https://gbatemp.net/threads/biskeydump-version-7-released-with-6-2-0-support.524542/ |source=https://github.com/rajkosto/biskeydump |donation= }} {{#seo: |title=Switch Homebrew PC...") |
No edit summary |
||
| (5 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
{{Infobox Switch Homebrews | {{Infobox Switch Homebrews | ||
|title= | |title=biskeydump | ||
|image= | |image=biskeydumpnx.png | ||
|description= | |description=Fusee payload that dumps your BIS keys. | ||
|author=rajkosto | |author=rajkosto | ||
|lastupdated=2019/06/22 | |lastupdated=2019/06/22 | ||
|type= | |type=Payload (Binaries) | ||
|version=9 | |version=9 | ||
|license=GPL-2.0 | |license=GPL-2.0 | ||
|download=https://dlhb.gamebrew.org/switchhomebrews/ | |download=https://dlhb.gamebrew.org/switchhomebrews/biskeydumpnx.7z?k33p0fil35 | ||
|website=https:// | |website=https://switchtools.sshnuke.net/ | ||
|source=https://github.com/rajkosto/biskeydump | |source=https://github.com/rajkosto/biskeydump | ||
|donation= | |donation=https://switchtools.sshnuke.net/ | ||
}} | }} | ||
Dumps all your Switch BIS keys for eMMC contents decryption, to be used as a fusee payload. | |||
| | |||
With all your BIS keys and your RawNand.bin (or the physical eMMC attached via microSD reader or using a mass storage gadget mode in u-boot/linux) you can explore/modify your eMMC partitions using [[HacDiskMount Switch|HacDiskMount]] by rajkosto (if running Windows). | |||
'''Note:''' The author is not responsible for anything, including dead Switches, loss of life, or total nuclear annihilation. | |||
==User guide== | |||
fusee | Send the biskeydump.bin to your Switch running in RCM mode via a fusee-launcher (sudo ./fusee-launcher.py biskeydump.bin or just drag and drop it onto TegraRcmSmash.exe on Windows) | ||
Either read out and note down the text printed on your Switch's screen, or scan the generated QR code with your phone to have a copy of all your device-specific keys | |||
Alternatively, use [[TegraRcmSmash Switch|TegraRcmSmash]] 1.1.0 or newer with a dummy argument so it keeps listening for usb comms, and you will get all the keys inside the console window, sample cmdline: | |||
<code>TegraRcmSmash.exe -w out/biskeydump.bin BOOT:0x0</code> | |||
==Screenshots== | ==Screenshots== | ||
https://dlhb.gamebrew.org/switchhomebrews/ | https://dlhb.gamebrew.org/switchhomebrews/biskeydumpnx2.png | ||
==Changelog== | ==Changelog== | ||
''' | '''v9 2019/06/22''' | ||
* First | *Support new tsec fw in 8.1.0. | ||
'''v8 2019/02/05''' | |||
Support new tsec fw in 7.0.0. | |||
'''v7 2018/11/27''' | |||
*Support new tsec fw in 6.2.0 and add option to save keys to microSD. | |||
'''v6 2018/05/04''' | |||
*Outputs dumped keys text to RCM host if it's listening. | |||
'''v5 2018/05/01''' | |||
*Validate retrieved keys by reading a keyblob and verifying its MAC. | |||
'''v4 2018/04/29''' | |||
*First compiled release (v4 and up get TSEC FW from eMMC boot0). | |||
== External links == | == External links == | ||
* | * Author's website - https://switchtools.sshnuke.net/ | ||
* | * GitHub - https://github.com/rajkosto/biskeydump | ||
Latest revision as of 01:27, 5 February 2024
| biskeydump | |
|---|---|
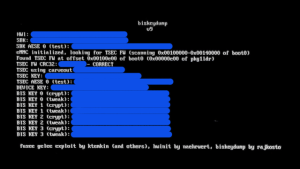 | |
| General | |
| Author | rajkosto |
| Type | Payload (Binaries) |
| Version | 9 |
| License | GPL-2.0 |
| Last Updated | 2019/06/22 |
| Links | |
| Download | |
| Website | |
| Source | |
| Support Author | |
Dumps all your Switch BIS keys for eMMC contents decryption, to be used as a fusee payload.
With all your BIS keys and your RawNand.bin (or the physical eMMC attached via microSD reader or using a mass storage gadget mode in u-boot/linux) you can explore/modify your eMMC partitions using HacDiskMount by rajkosto (if running Windows).
Note: The author is not responsible for anything, including dead Switches, loss of life, or total nuclear annihilation.
User guide
Send the biskeydump.bin to your Switch running in RCM mode via a fusee-launcher (sudo ./fusee-launcher.py biskeydump.bin or just drag and drop it onto TegraRcmSmash.exe on Windows)
Either read out and note down the text printed on your Switch's screen, or scan the generated QR code with your phone to have a copy of all your device-specific keys
Alternatively, use TegraRcmSmash 1.1.0 or newer with a dummy argument so it keeps listening for usb comms, and you will get all the keys inside the console window, sample cmdline:
TegraRcmSmash.exe -w out/biskeydump.bin BOOT:0x0
Screenshots
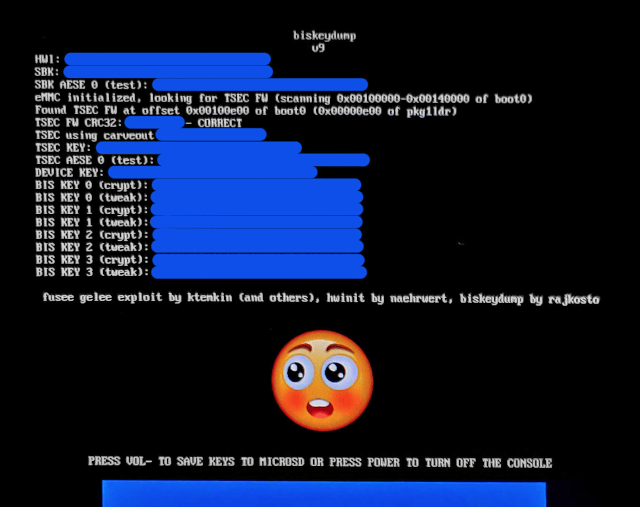
Changelog
v9 2019/06/22
- Support new tsec fw in 8.1.0.
v8 2019/02/05 Support new tsec fw in 7.0.0. v7 2018/11/27
- Support new tsec fw in 6.2.0 and add option to save keys to microSD.
v6 2018/05/04
- Outputs dumped keys text to RCM host if it's listening.
v5 2018/05/01
- Validate retrieved keys by reading a keyblob and verifying its MAC.
v4 2018/04/29
- First compiled release (v4 and up get TSEC FW from eMMC boot0).
External links
- Author's website - https://switchtools.sshnuke.net/
- GitHub - https://github.com/rajkosto/biskeydump
